Demonstrate Quantum Encryption With a Flashlight and Pair of Sunglasses
"Are you telling me that this could be of practical use?" exclaimed the Irish physicist John Bell. He had shown in the 1960s that quantum entanglement burrowed deep into the foundations of physics, but even he hadn't thought it could have real-world applications. That was the brainstorm of Artur Ekert, then a graduate student at the University of Oxford, who came up to Bell after a talk in 1989 and explained it to him. The episode was entertainingly recounted by Louisa Gilder in her book The Age of Entanglement. "Well, it's unbelievable," Bell said.
Last month, while visiting Ekert at the Centre for Quantum Technologies in Singapore, along with Howard Wiseman and the labs at the Centre for Quantum Dynamics at Griffith University in Brisbane, I got an idea for how to demonstrate quantum cryptography using ordinary household items. The improvised setup is several steps removed from true quantum crypto, which is still a graduate-student-level project, but it involves the same physics and, in principle, could be upgraded to the real deal by swapping in more advanced components. The demonstrator is a classical version of the cryptographic scheme invented in 1984 by Charles Bennett and Gilles Brassard. It encodes a message using the polarization of light. If government agents or nosy siblings try to intercept the signal, they'll muck it up and thereby betray themselves.
You'll need the following:
Two linear polarizers. I bought 2-inch-diameter polarizers from Edmund Scientific. You could also break out the lenses from a pair of polarizing sunglasses or IMAX 3-D googles, buy polarizing film from an outlet such as Ward's Science, or repurpose the polarizing filters that screw onto the front of 35mm camera lenses.
Two pieces of cardboard, each about twice the width of the polarizers
Flashlight
White index card, to serve as a screen
Some way to hold the components steady. I used an alligator-clip holder from Radio Shack, but binder clips would probably work, too.
Two coins or random-number generators
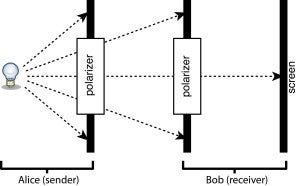
The sender ("Alice") encodes the message with one polarizer; the receiver ("Bob") decodes it with the other. If the polarizers are not already circular, cut them to be so. Mount each in a piece of cardboard to block stray light and to make it easier to handle. Cut a hole in the cardboard a bit smaller than the polarizer and tape it in place. The orientation of the polarizers is important; be sure to mount both in the same way. I'd recommend trimming the cardboard into an octagon, so that you can rotate it in 45-degree increments. Mark four directions: horizontal (0 degrees), diagonal (45 degrees), vertical (90 degrees), and "antidiagonal," meaning diagonal the other way (145 degrees).
Align the flashlight, polarizers, and index card. To verify the setup, align the polarizers in the same direction and turn on the flashlight. Fine-tune the position of the components until you see a fairly bright circle on the screen. You might need to dim the room lights.


Then, rotate one polarizer by 45 degrees. The circle should dim subtly but perceptibly. If you measure its brightness using a light meter, it should halve in brightness.

Rotate the polarizer another 45 degrees, so that the two polarizers are now perpendicular. The screen should go completely dark.
Now we can use this little apparatus to send a message. The most straightforward approach is to translate the message into a string of bits and encode '0' as horizontal polarization and '1' as vertical polarization. For each bit, Alice turns her polarizer to the appropriate position. Bob parks his polarizer in the horizontal position and leaves it there. He records a '0' if the screen is bright and '1' if it is dark. After giving him enough time to take the reading, Alice goes to the next bit and continues until the message is sent.
As a means of communication, this might sound needlessly baroque. Why not simply flash the light on and off like Morse code? In laser communications, engineers have found that polarization can be a more robust carrier of information than the presence or absence of light, since atmospheric turbulence can alter its intensity of a light beam, but leaves its polarization unaffected. More important for our present purposes, the scheme translates directly to the quantum realm: it works even if you make the light source so dim that the bits are being carried by single photons.
Be that as it may, the scheme is totally insecure. An eavesdropper ("Eve") can intercept the beam with her own polarizers and flashlight. First she follows the same procedure as Bob to record a bit. Then she follows the same procedure as Alice to retransmit that bit to Bob. She allows herself an evil chuckle as her interference goes undetected.
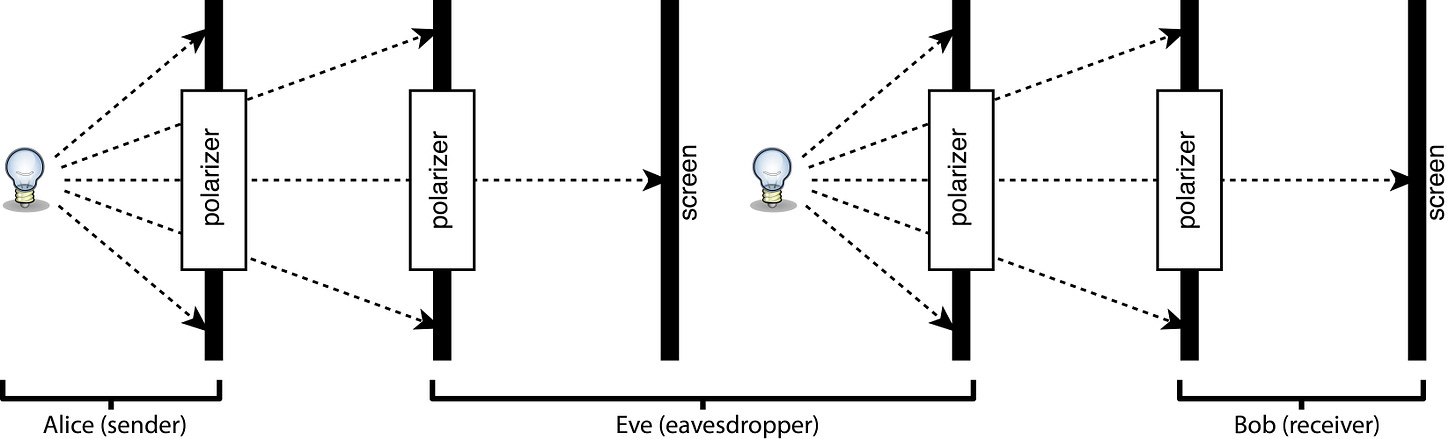
Quantum cryptography seeks to foil Eve by introducing an element of randomness, which we can simulate by giving Alice and Bob coins to flip. In this more sophisticated scheme, Alice doesn't transmit her message just yet—she first establishes the security of the channel by sending a string of test bits. For each, Alice flips her coin, and if it lands on heads, she uses the same encoding as before: '0' is horizontal polarization, '1' is vertical. For tails, she switches to a new convention: '0' is diagonal polarization, '1' is antidiagonal. Bob likewise flips a coin, orients his polarizer either horizontally or diagonally, and records a '0' if the screen is bright and '1' if dark. If the spot is intermediate in luminosity, he treats it as ambiguous and flips the coin a second time to record a '0' or a '1' at random. (This is the trickiest part of the procedure. Bob needs to reliably tell the difference between full and half brightness, which look very similar to the human eye.)
After Alice finishes sending her test bits, she uses some ordinary means of communication to tell Bob the results of her coin tosses. The two needn't worry about anyone listening in on this communication; on its own, it gives nothing away. Whenever their results match—half the time, on average—Bob can be assured that his reading accurately reflects Alice's transmission. The rest of the time, his readings are random noise and he crosses them out. Of the bits he does trust, he takes a sample and confirms with Alice that they were indeed what she sent.
Now Eve is going to have a harder time of it. In making her own measurement, she needs to choose whether to orient her polarizer horizontally or diagonally, and on average her choice will match Bob's only half the time. So she won't be able to intercept and retransmit the bits reliably. When Alice and Bob perform their verification step, they will find that only half the test bits got through, and they'll know their line is being tapped. They can use the bits that did get through as a secure key for subsequent transmissions. The following animation from the Centre for Quantum Technologies elegantly illustrates the procedure. (In the video, the quantum key generator is shown separate from Alice, whereas the simple demonstrator combines these two functions.)
Because the simple demonstrator is not truly quantum, it is vulnerable to a cleverer eavesdropper. The difficulty of distinguishing full from half brightness is a weak point that Eve could try to exploit. She could also bleed off a bit of the light using a partially silvered mirror, and Bob might never know his signal was being tampered with. Such surveillance strategies become impossible only when you go to the level of individual photons, where there's nothing left to bleed. Several cities now have quantum secure networks.
To be sure, even real quantum cryptography is not as foolproof as sometimes claimed. The Bennett-Brassard scheme can be hacked by exploiting the inevitable imperfections in the equipment. The nice thing about Ekert's procedure is that it adds the element of nonlocality, which provides a way to corroborate that the procedure works even if imperfectly implemented.
